Tracing Ghostly Ether the Other Way
On the liquidity mining variant of pig butchering scams and following the gas
Note: I semi-apologize for a long gap, as I’ve recently been consumed by a research project that will hopefully make a small splash when it gets published
Follow the Gas Money
A New Mode of Scamming
Made in Chinese Fraud Factories
Who got approved?
Follow the Gas Money
Many victims of pig butchering scams found that they just became one when their cryptos magically disappear from their Coinbase Wallet app. They didn’t send out anything, and they certainly didn’t share their private key or seed phrase to anyone. What happened?
Crypto, like money, doesn’t move by itself. There are no ghosts or poltergeists in Ethereum. No uncaused cause there. There will always be (1) someone moving it and (2) ‘gas’ fees for transferring anything in the Ethereum blockchain. The hidden hand will leave traces that way. This is one of the ways blockchains can be interesting.
To review, USDT is a token on the blockchain, and one USDT signifies one US dollar held by the company Tether. (See smart contracts and joojoos). In almost all cases, one must have ETH to spend for gas to move any amount of USDT from one crypto address to another. Those ETH have to come from somewhere.
Scammers creating new crypto addresses to launder USDT have to first invest some ETH into that address, if not provided by a scam victim. Those ETH can sometimes come from surprising places. ‘Following the money’ can be more than just following a victim’s stolen crypto. Sometimes, you can get lucky tracing upstream for who’s paying the gas fees.
In fact, with the infamous cryptocurrency anonymizing tool Tornado Cash, tracing who is paying the gas to withdraw laundered cryptos from it can give away the user’s identity. Tornado Cash gets around this by employing paid third-party “relayers”, which is just another money service business, no?1 (Among the reasons the US DOJ is suing the Tornado Cash founders.2) So much for “disintermediation” and “decentralization”…
In the case of common pig-butchering scams, looking at gas might be helpful, though only if you can confidently identify ETH meant for gas, and if it can be reliably traced to a compliant exchange. Thinking about gas can also be useful in investigating the “liquidity mining pool” variant of pig butchering scams.
A New Mode of Scamming
“Liquidity mining” scams is a later variant of pig butchering scams, incorporating elements of blockchain technology into a social engineering scheme.
Prior to it, pig butchering scammers were quite conventional in using cryptocurrency, using it like bank wire frauds. Victims are tricked into sending payments to an account the scammers control, be it a crypto address or a bank account. With liquidity mining scams now though, scammers are taking advantage of smart contracts.
What is a liquidity mining pool? If you really want to know, Google it. What exactly it is doesn't really matter here. I can call it "jamba wamba", and if you stake your USDT to "jamba wamba", your 1,000 joojoo will grow 1,200 joojoo, 2,000 joojoo, 10,000 joojoo, or whatever the scammer tells you.
You will have to know what cryptocurrency wallets and dApps are. A cryptocurrency wallet is essentially software for managing the cryptocurrency addresses. But more than that, wallets allow for direct interaction of your wallets’ contents with smart contracts for e.g. automating payments, swapping tokens. Meanwhile, dApps or decentralized apps are simply apps not hosted on one server, so that no evil corporation can easily take them down. Smart contract code live on the blockchain, and dApps serve as their snazzy user interface. It's only fitting to have decentralized, censorship-resistant user interfaces for decentralized, censorship-resistant blockchains.
Liquidity mining scam works as follows:
It starts the same way as with any pig butchering scam, with scammers finding targets on dating, messaging, or social apps, grooming them over time, and teaching them crypto. But instead of victims being tricked to send cryptos to the scammers’ accounts, victims are convinced to download their own crypto wallet from app stores and to deposit money (cryptos) into it. Ostensibly, victims feel safe having full custody of their cryptos. The scammers would emphasize this point as much, and it is true.
But then victims are told to connect their wallets to a “liquidity mining pool”, so they can start participating in its rewards. Crucially, when connecting to the dApp, the victim unknowingly gives unlimited token approval (approval to move unlimited tokens) to the scammer. Well, the dApp is a smokescreen, and the "mining pool" doesn't really exist.
Normally, token approvals are used in non-malicious dApps to pre-approve payments, exchange tokens, stake, etc. In liquidity mining scams, unlimited token approval is requested, disguised as a small service fee, connection fee, or "mining certificate". This is akin to a phishing attack in traditional computer security terms.
Note that the victim has not shared their private key and has not initiated transfers out of his/her wallet. Nevertheless, with unlimited token approval the fraudsters can now drain the entire contents of the victim's wallet address at will at any time.
All that remains for the scammers is to keep persuading their victim to load up on his/her wallet. Say for example, the higher the deposits, the higher the yield. Other tricks are showing fake earnings on the dApp screen display, asking withdrawal fees or "taxes", and/or sending back worthless, counterfeit USDT tokens as the profits. The scammers do not have to drain the victim's wallet immediately, in order to keep up the charade and maximize the final theft.
Made in Chinese Fraud Factories
The liquidity mining scams are conducted wholesale by the same Chinese pig butchering scam syndicates in Southeast Asia. Based on human sources there and in illicit Telegram groups, their criminal tech developers developed this way of scamming in late 2021, as seen below in a contemporary instruction manual for scammers:

Total losses to the mining pool version of pig butchering scams has been at least $388 million to date, according to a Dune Analytics dashboard tracker that displays a running daily tally of losses to pig butchering liquidity mining scams (USDT Approval Mining, Liquidity Mining & Sha Zhu Pans). It has found ~25,000 victims of liquidity mining scams, and the largest single victim loss to it is $9.7 million.
Importantly, the tracker counts only USDT losses, and it must be said that it does not include direct transfers made by victims themselves, nor any stolen ETH, Bitcoin and USDC (another USD-pegged stablecoin). The tracker looks to be made by an associate of MetaMask, a popular cryptocurrency wallet app. From experience and a news report though, I know a majority of liquidity mining scam victims were Coinbase Wallet app users.
It is also mostly looking at scams most active for 10 months in 2021-2022. Up to now, liquidity mining scams peddled by pretty Asian profiles online are still rampant, with appeals from its latest victims for help coming almost every week on Reddit.
Who got approved?
To where are token approvals sent? Yes, token approval costs gas, too. When a victim (inadvertently) gives token approval, it takes the form of some ETH going from the victim address to a scammer-controlled address, authorizing that scammer address to spend the USDT content inside the victim’s address.
That approved spender address is typically not the receiving address that the scammer moves money to. Scammer receiving addresses are typically not used for long, but approved spender addresses are re-used by scammers many, many times.
One can see any approved spender of an address using Etherscan.io, under More —> Services —> Token Approvals. Also on revoke.cash
The Dune Analytics dashboard above actually tracks approved spender addresses, to whom the victims unwittingly approved to control their wallets. Amazingly, only about 200 approved spenders account for all those losses.
Now, for the approved spender to move victim USDT around, he/she must be consuming some ETH. The hidden hand have to prime his approved spender address with ETH. Where did that ETH come from?
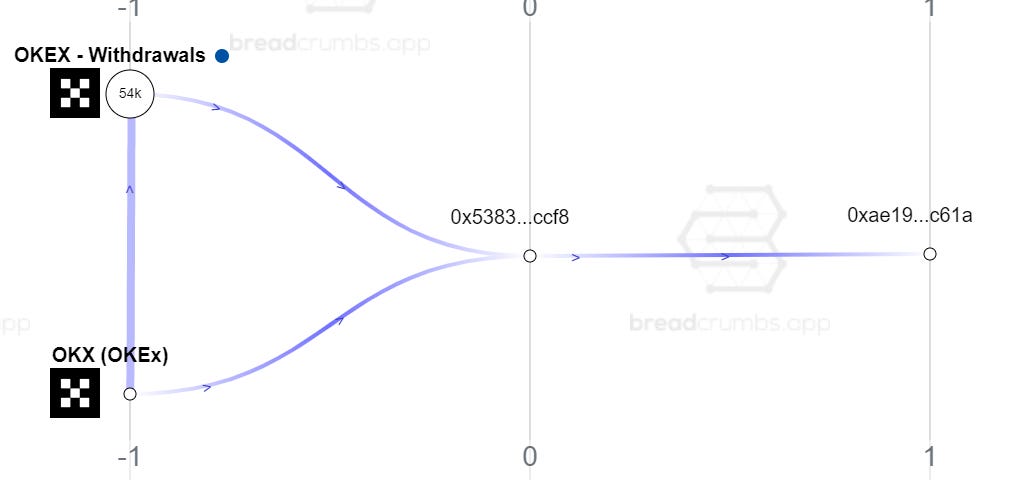
The approved spender seems to be an OKX customer. A good target to subpoena? Good luck convincing a 70-year old judge to approve that.
Below is another scammer approved spender address, taken from the abovementioned Dune Analytics dashboard and responsible for stealing from multiple victims. He looks like a Binance user(s).
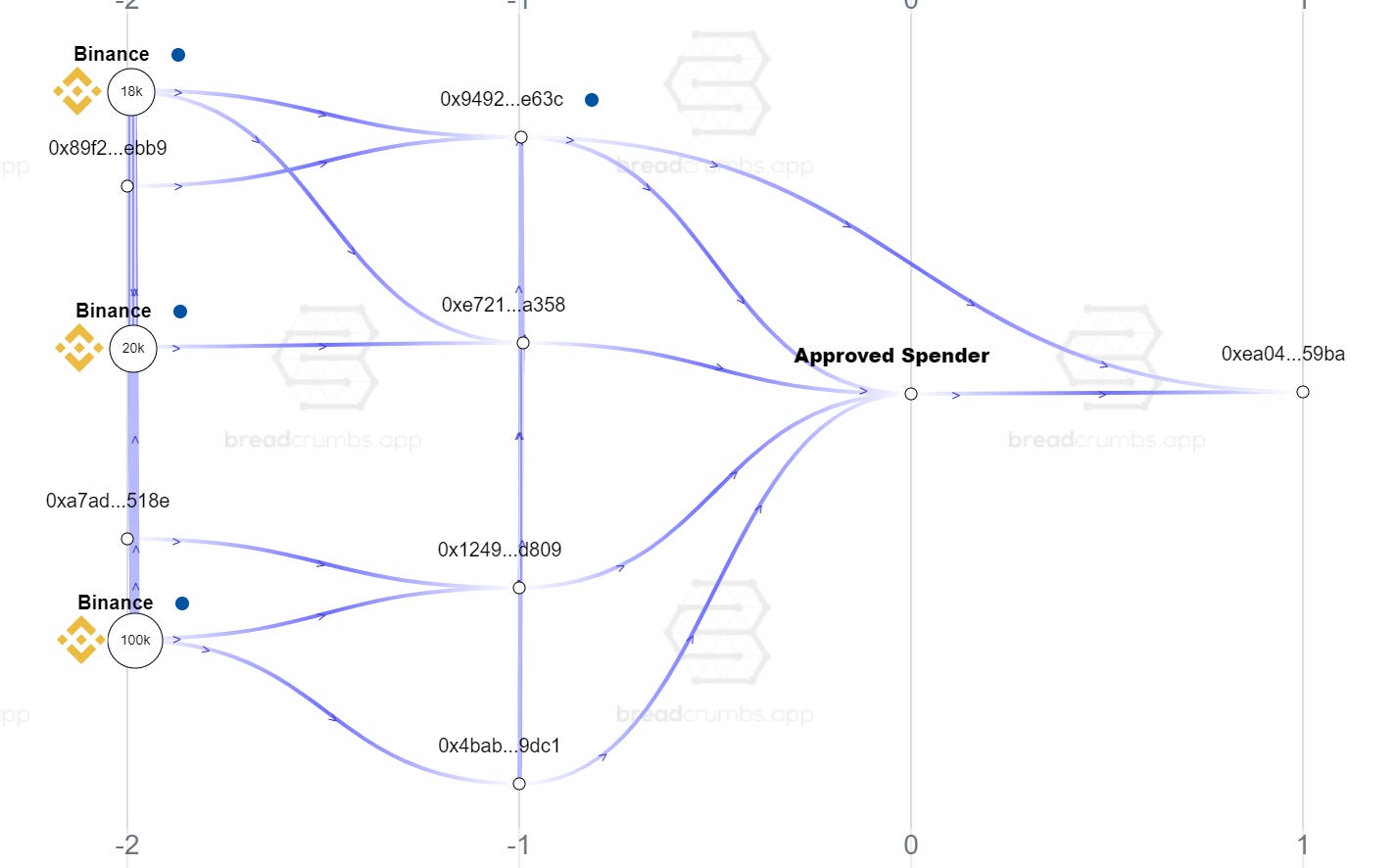
Scammers are prepared for people following the scammed money, and so they’d throw some obfuscation and money mules behind them. They might not be so careful though with their gas money. You bet that the people sending ETH to approved spender addresses must know what the ETH is for, if they’re not the hidden hand themselves.
Caveat Emptor!
For some tokens like USDC, they can have so-called ‘permit signatures’ that do not need gas for approval! The approval process is ‘gas-less’ and happens off-chain! It won’t show up in an victim address’ list of approved spenders!
However, while the approval process itself leaves no trace on-chain, moving USDC or any tokens still needs gas, and the approved spender address can still be discovered in the transaction log when the USDC was stolen. See case study and references3.
The Wild West of crypto is a dangerous place.
UP NEXT: How-to launder money using TRON (maybe)
awnflkfndslnwae;ovc WVOINAEOVN[N[V







This is an incredibly insightful analysis, the fact keys are never shared should get people's attention- appreciate the "real talk" on the prosecution (sad but true from my experience). Thank you for sharing!